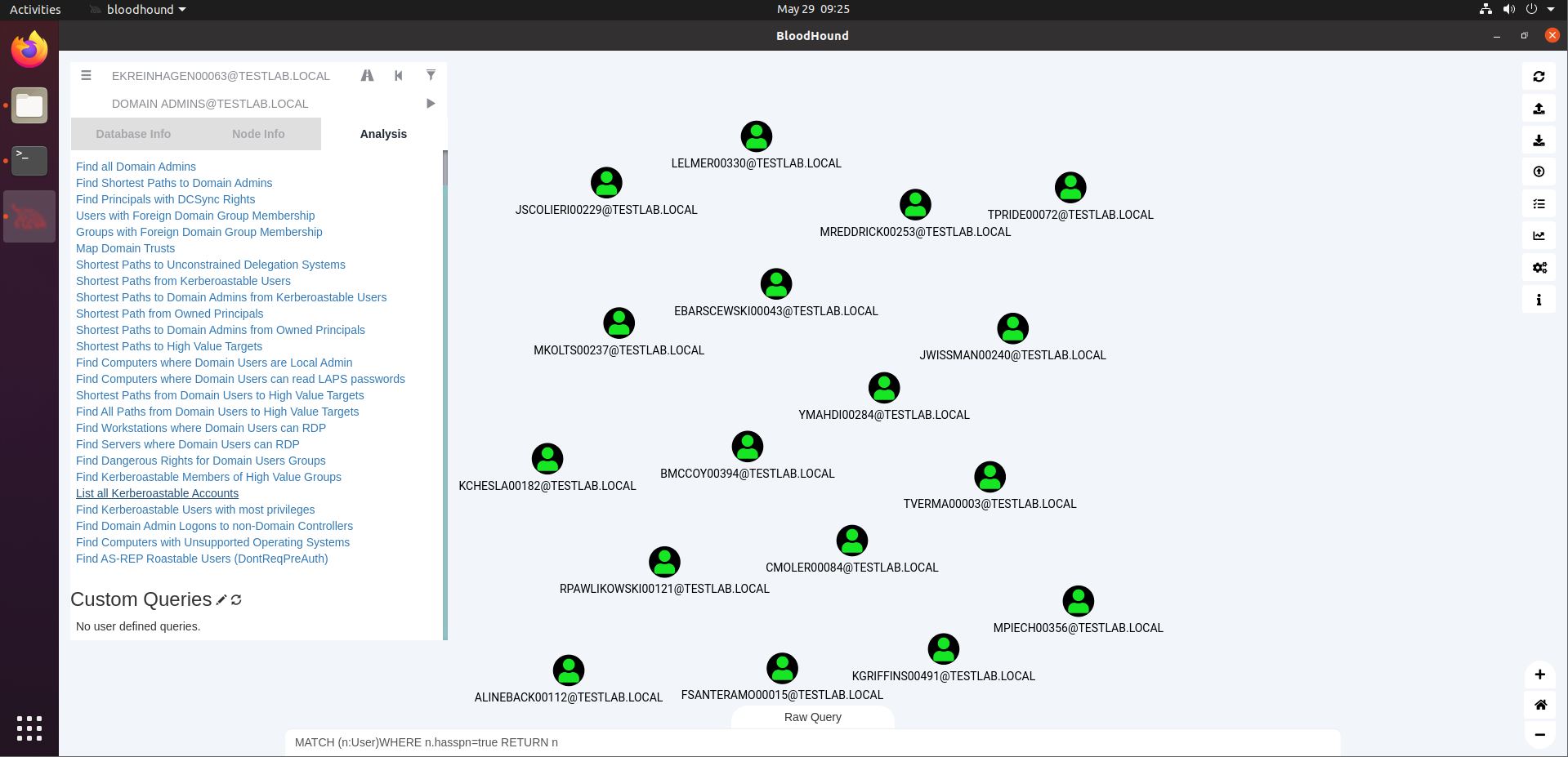
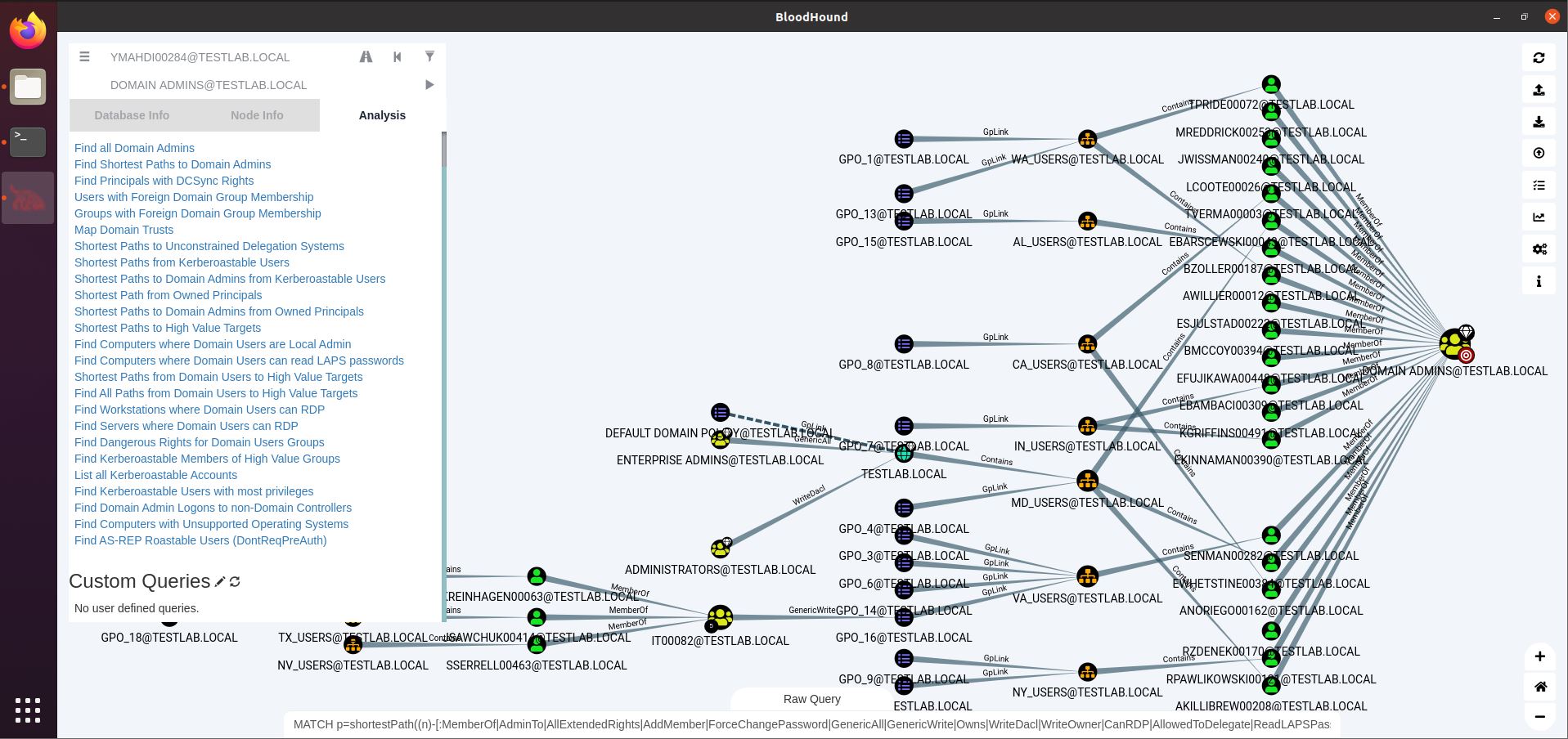
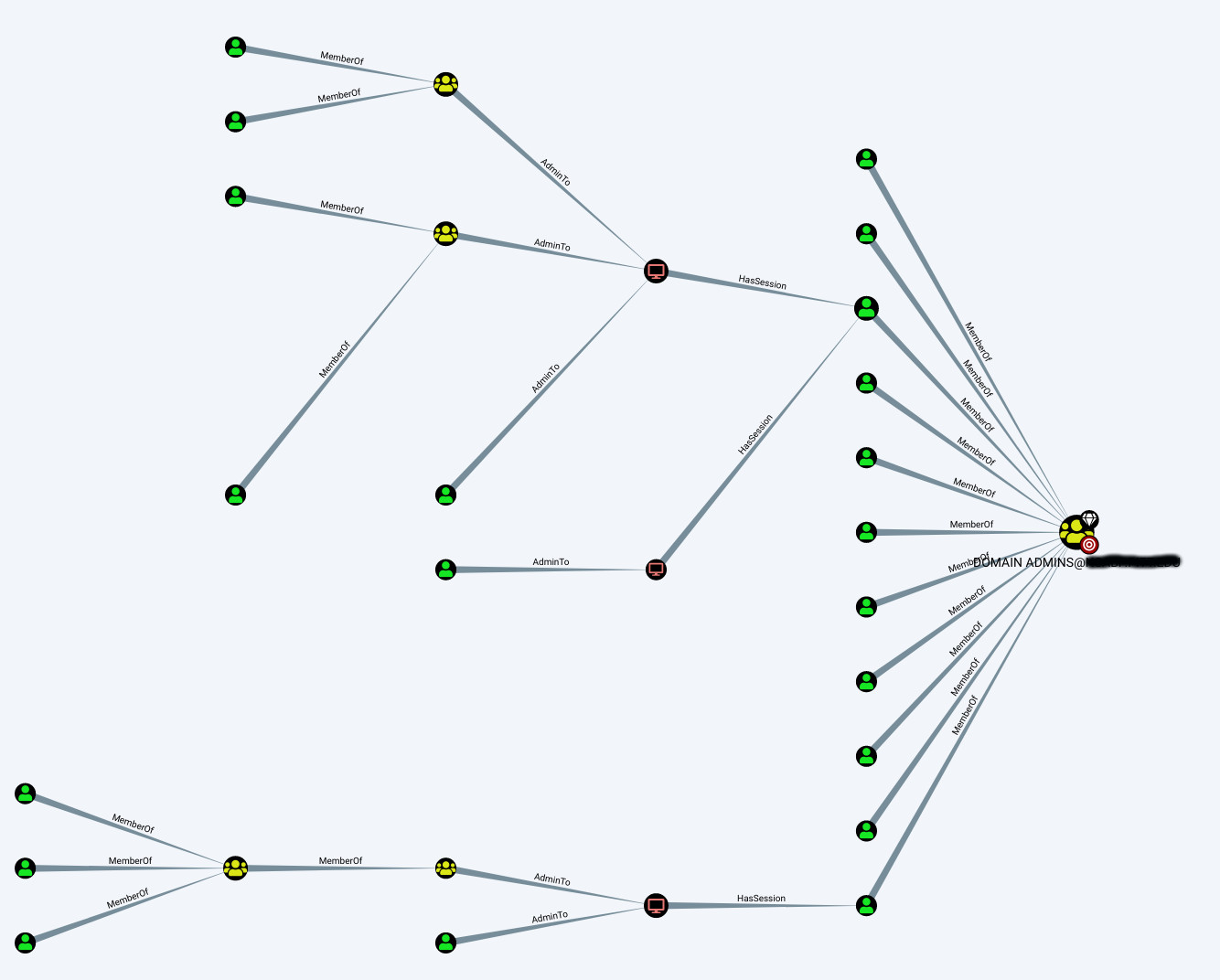
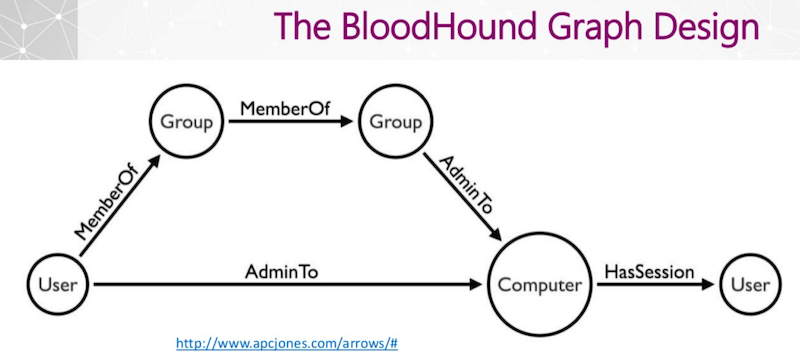
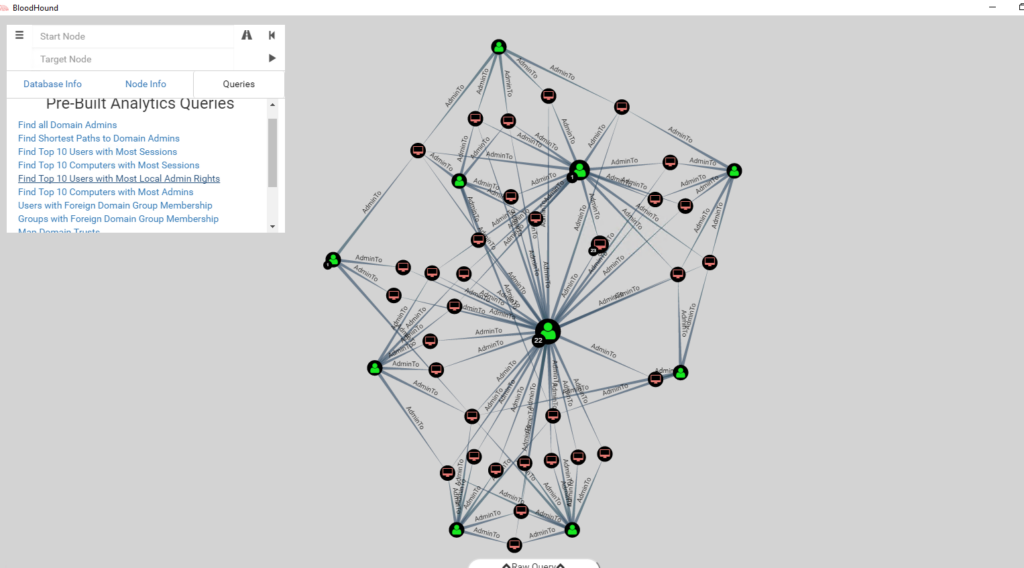
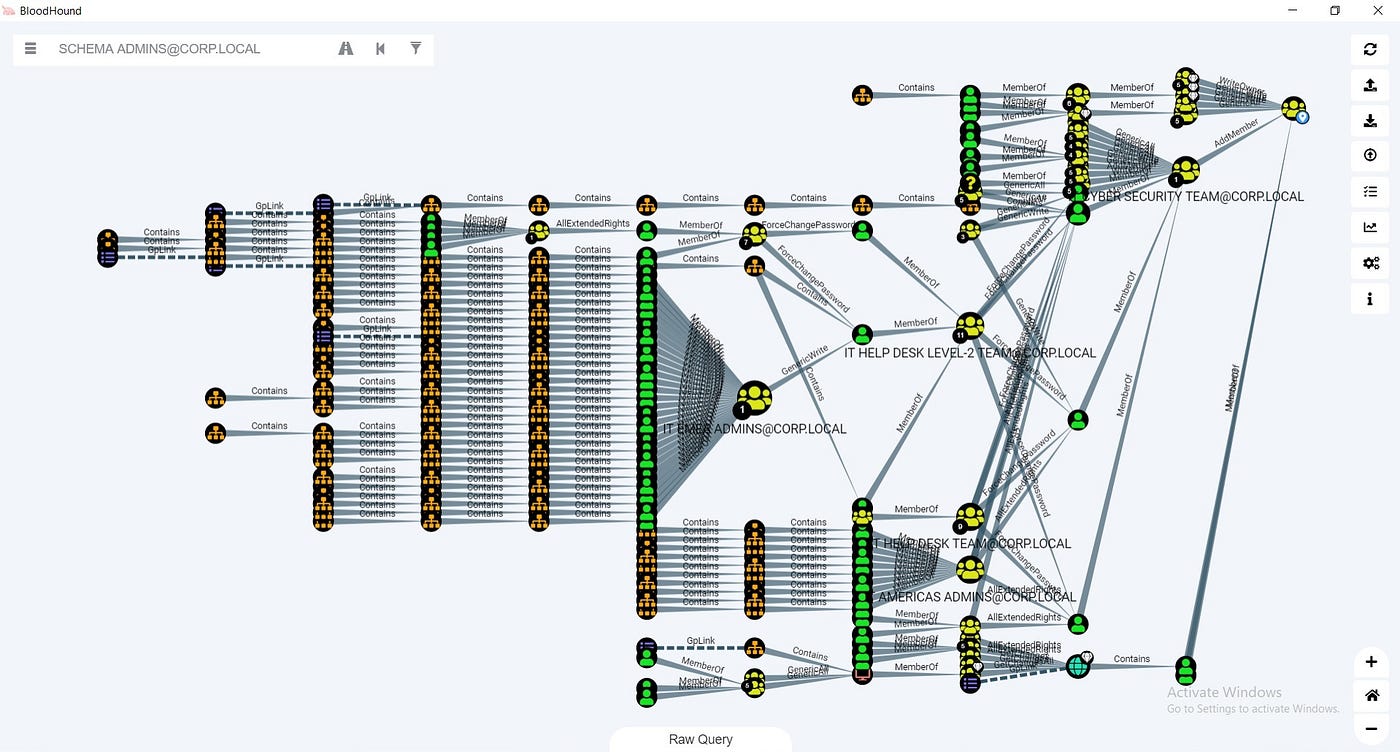
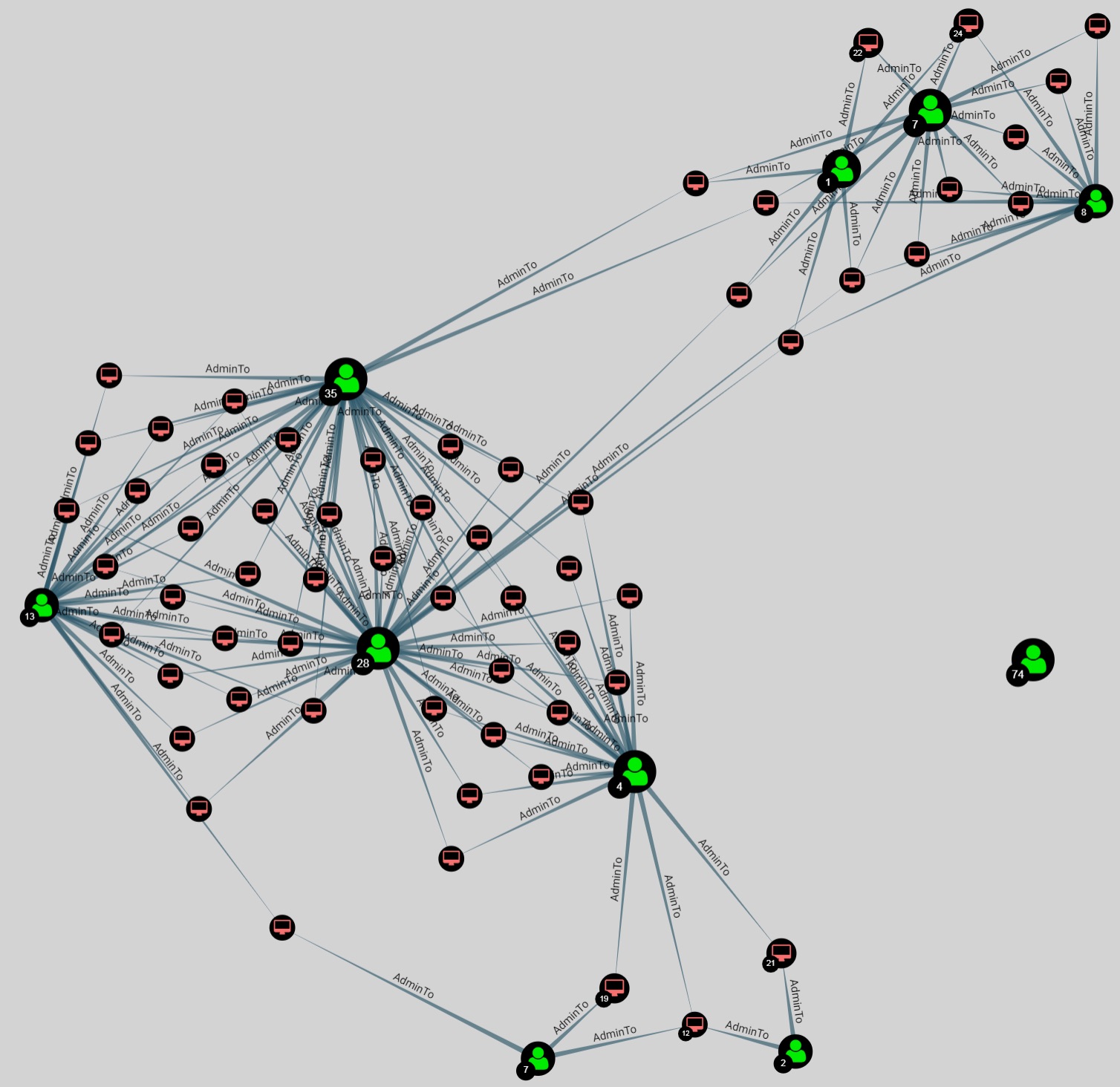
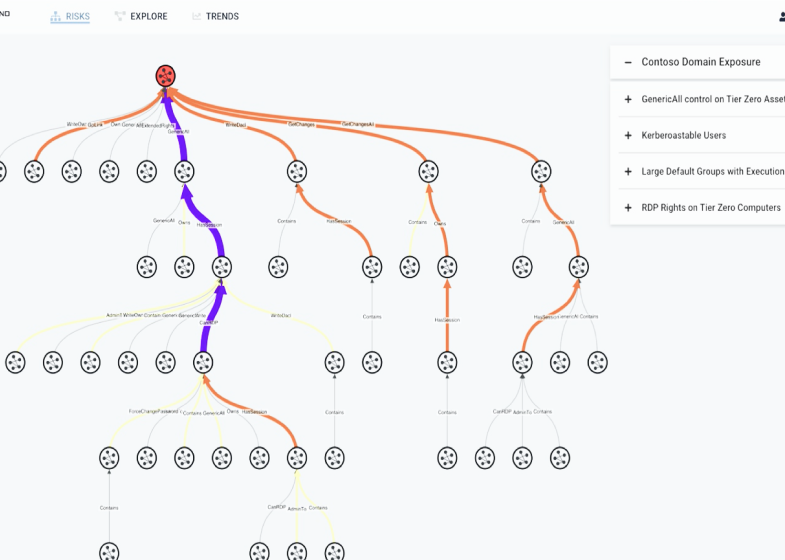
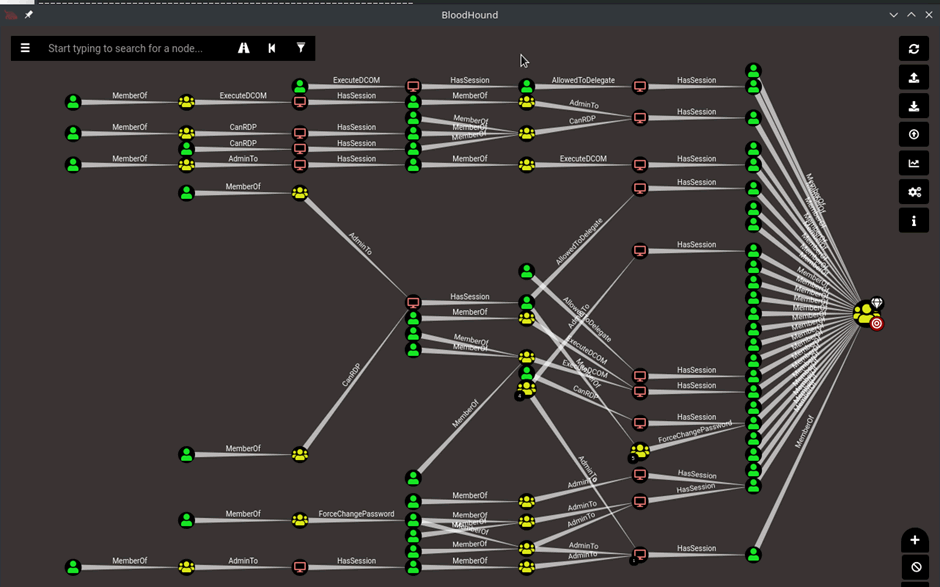
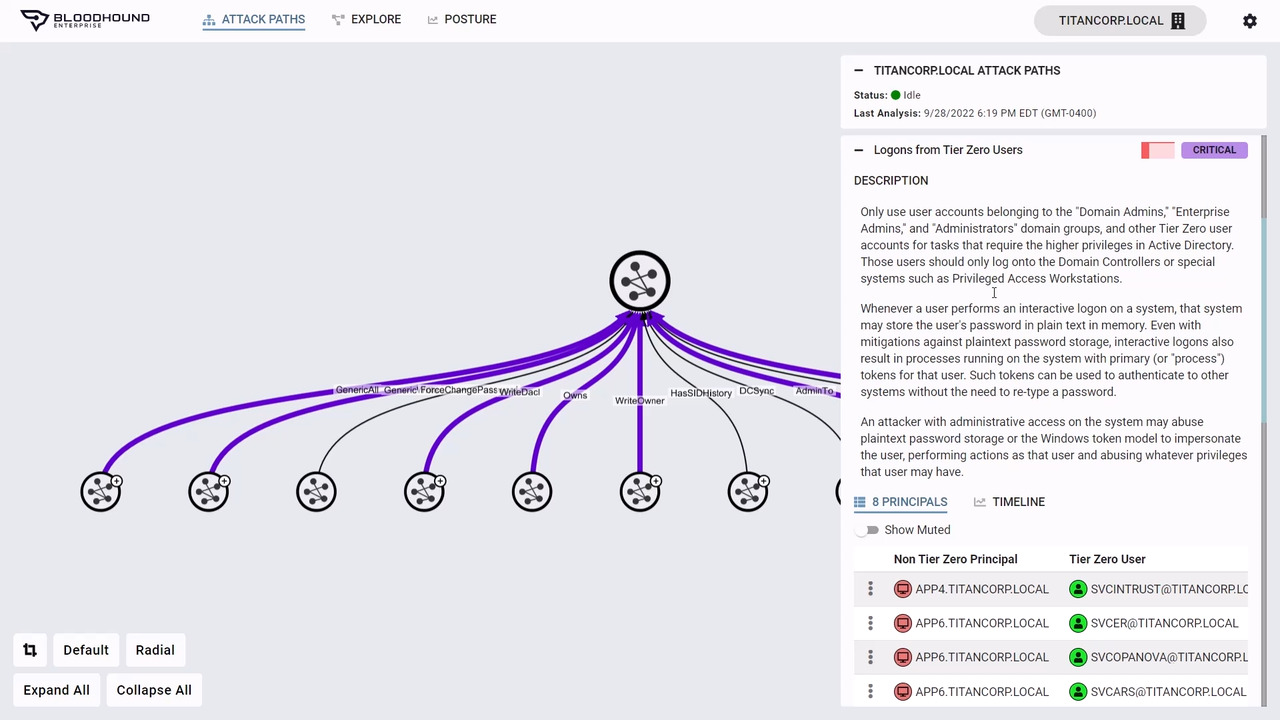
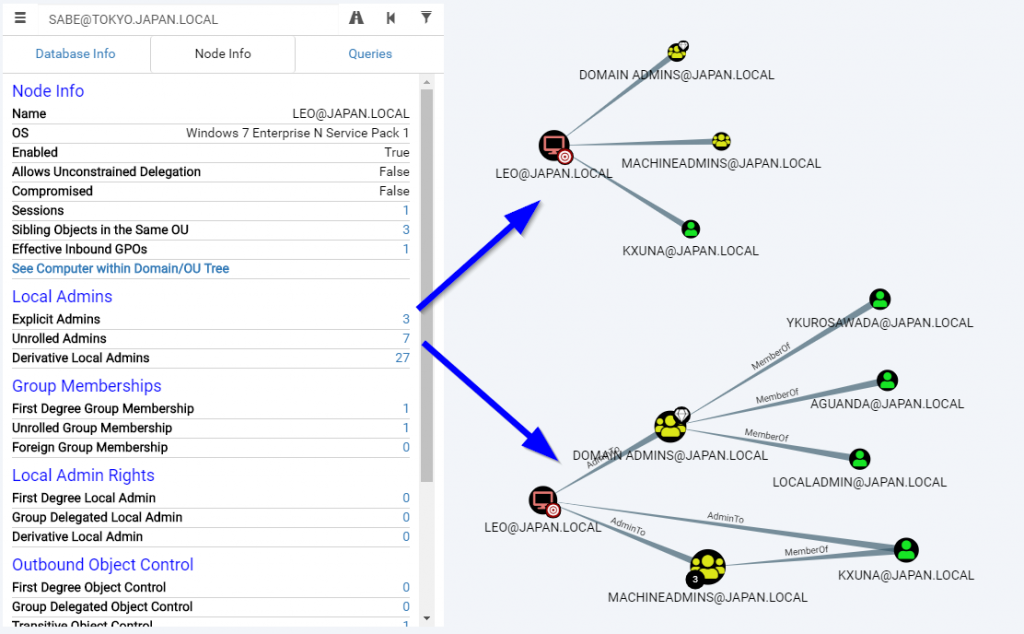
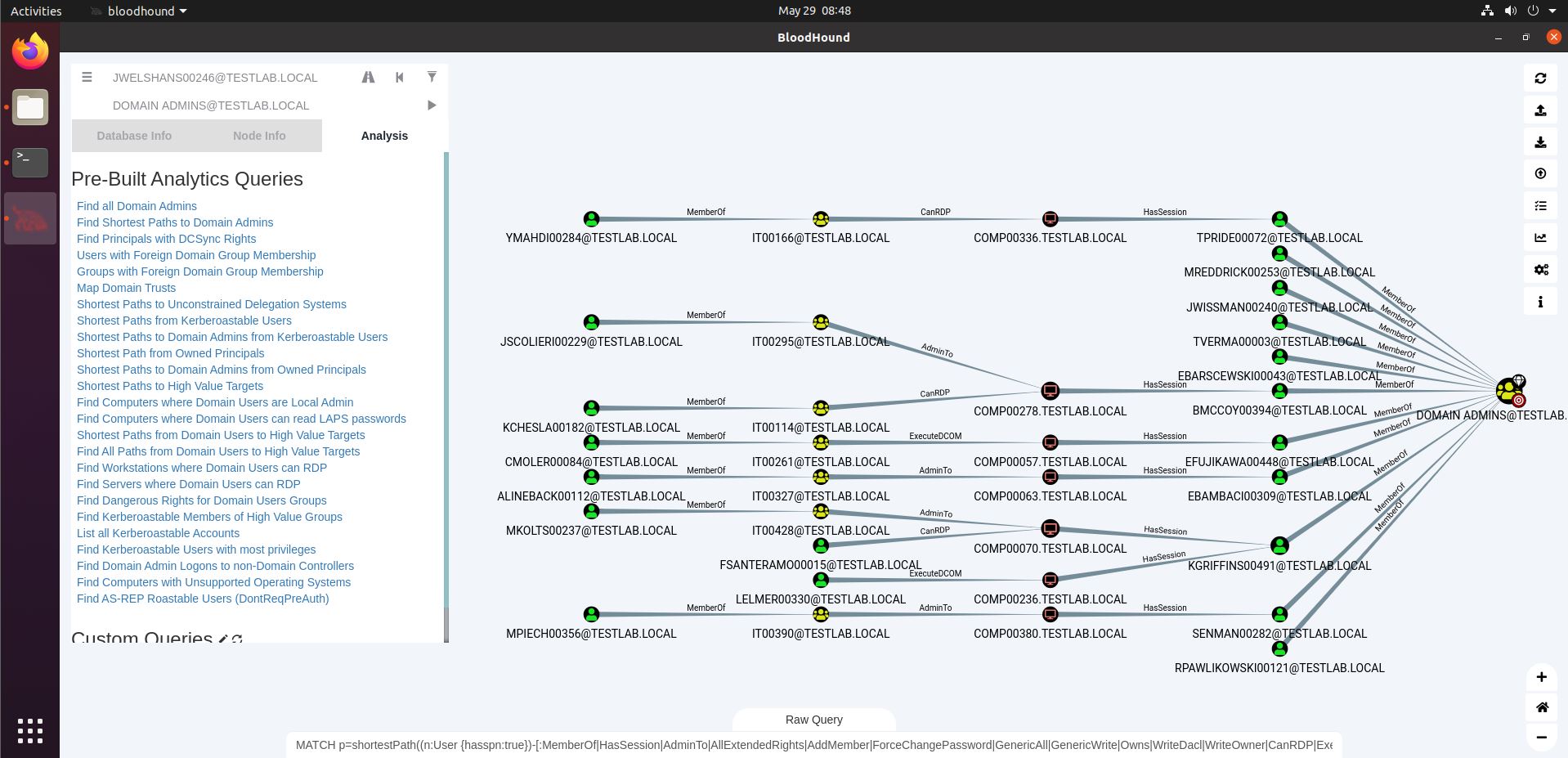
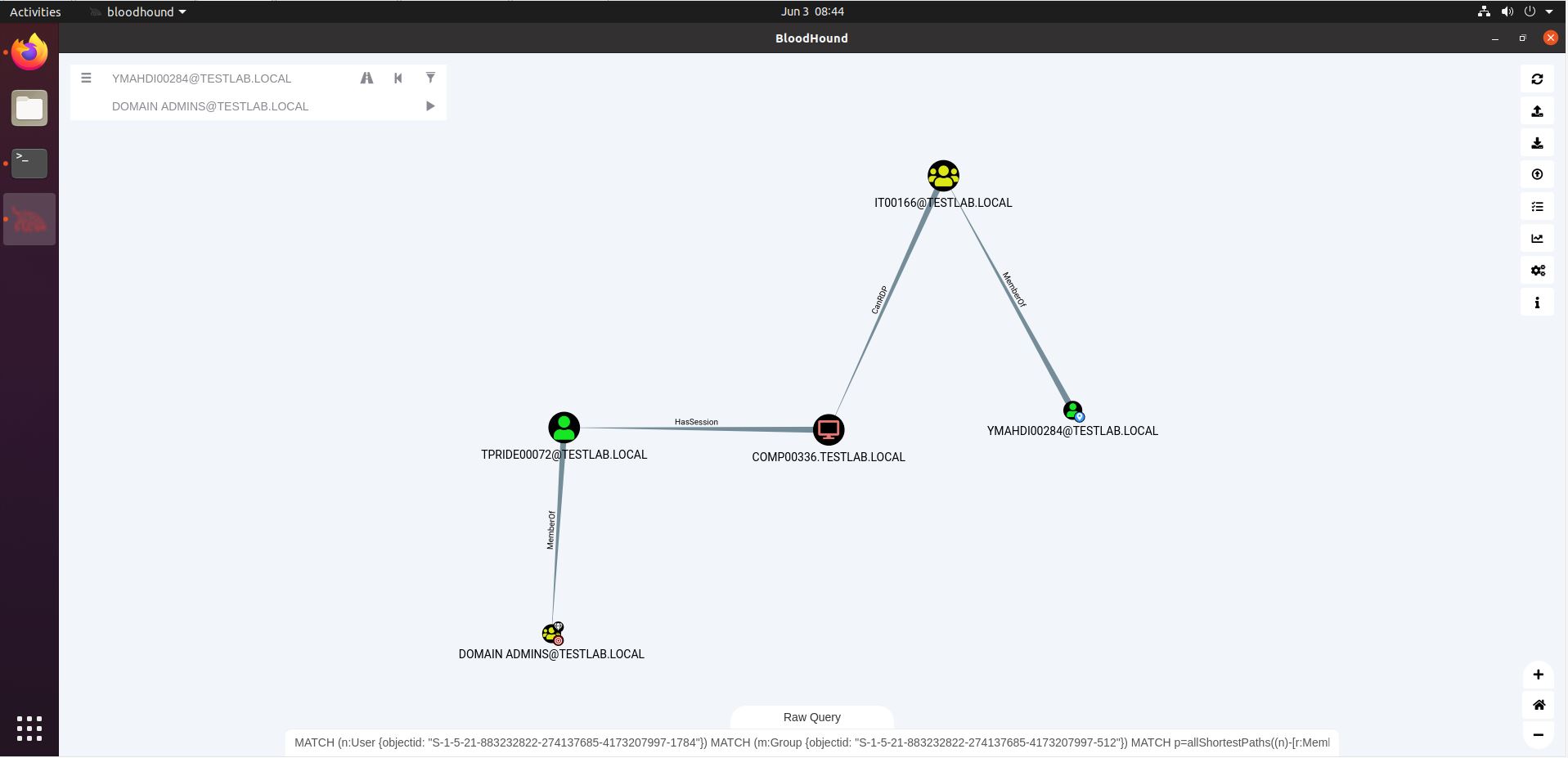
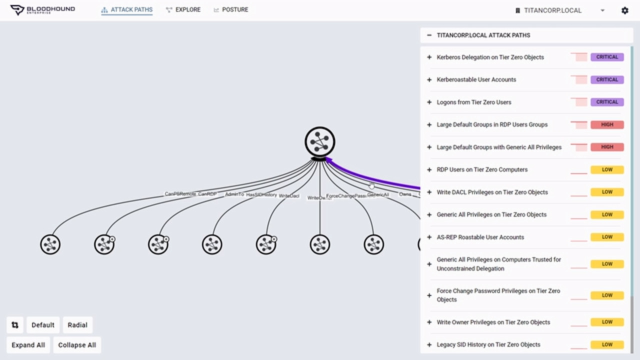
Entity Based Detection Engineering with BloodHound Enterprise | by Joshua Prager | Posts By SpecterOps Team Members
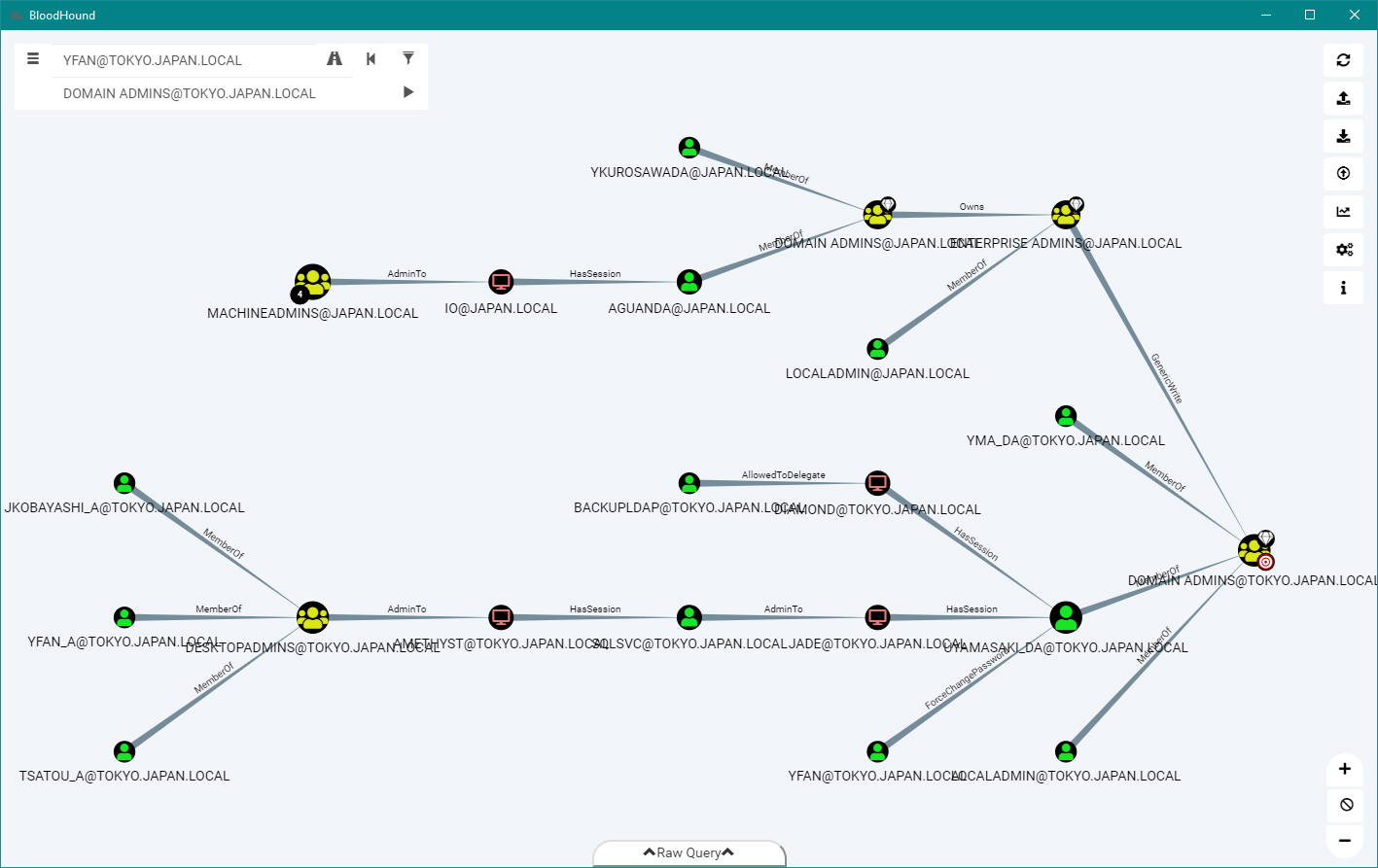
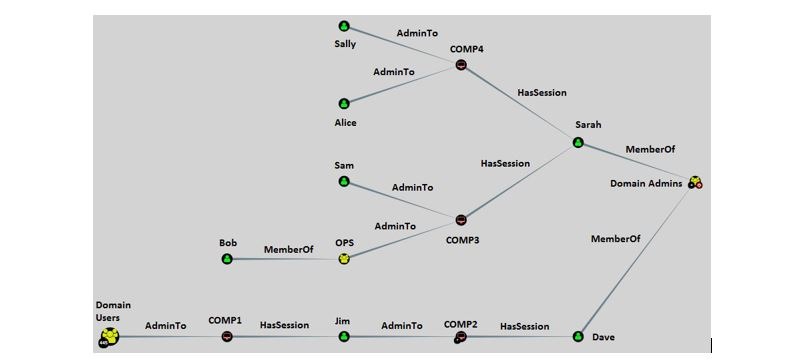
How Attackers Use BloodHound To Get Active Directory Domain Admin Access -- Microsoft Certified Professional Magazine Online